Charles Sturt University - Master of Cyber Security
Date Earned: August 15, 2021
Linky: https://itmasters.edu.au/course/master-of-cyber-security/
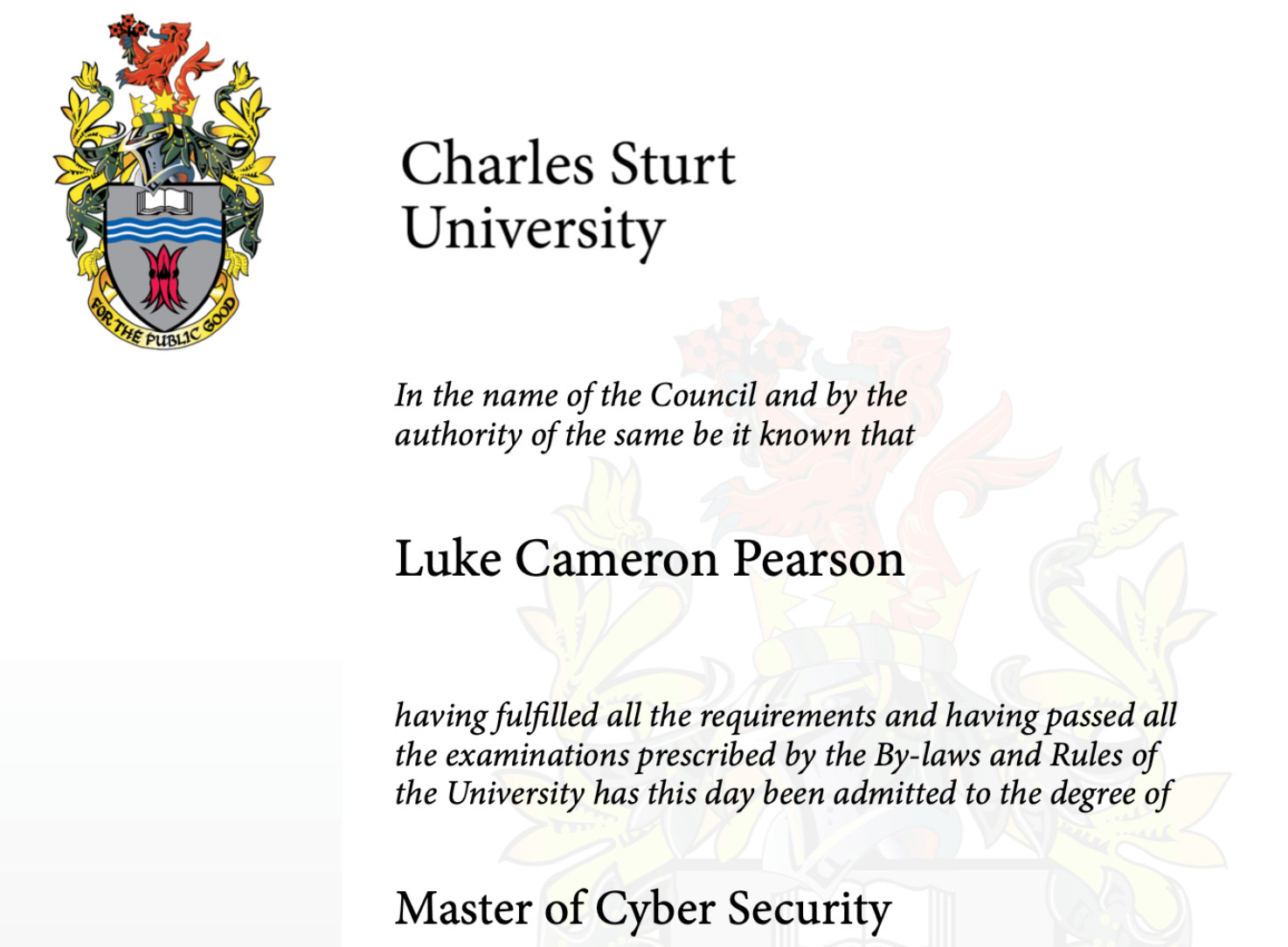
Oh no! You know my middle name is Cameron!
This review is from the point of view of a mature aged student who already had a good deal of cyber security experience when starting study. This course required 12 classes to be undertaken and passed to have enough credits to pass the Masters. I applied for Recognition of Prior Learning (RPL) to six of these classes, in the form of:- [CISSP]({{ $baseurl }}/isc2-cissp/) (two credits)- Sec+ (one credit)- ACS Certified Professional (two credits)- ISFCE CCE (one credit)
I signed up through the IT Masters scheme.
Who’s it for?
I’d recommend this Masters degree to anyone who wants to learn how to perform literature-based research, and gain or improve their formal writing capabilities. Outside these things, there are much better learning options for every class I took through uni except Network Security and Cryptography.
Training
Network Security and Cryptography
I was super lucky in getting Michael Bewong as the professor for this class. Michael taught us about cryptography, from the history of (rail fence, Caesar, etc) through to best in practice today (AES, RSA, etc). We get to perform RSA encryption, decryption and key generation by hand, which made me feel like a proper nerd (in a good way).
Following that, we move on to network based authentication mechanisms, with NTLM and Kerberos. We learn the cryptographic principles underlying these technologies and how they can be attacked.
The prescribed text for this class was Cryptography and Network Security: Principles and Practice, and it was pretty great.
Hacking Countermeasures
This course was a watered down CEH. It covered the hacker mindset, and a range of tools. One assignment had us building a USB bourne password extractor, that could be used in conjunction with a social engineering attack. While a cool exercise, everything in this course would have been accomplished with CEH prep and an afternoon of google.
The prescribed text for this class was the CEH Certified Ethical Hacker All-in-One Exam Guide, Fourth Edition.
Dark Web
I hated this class with a passion. The content was largely around cyber crime, with a splash of TOR. The prescribed text for this class was Inside the Dark Web, which was authored by the professor and assistant. It reads like a collection of uni papers smushed together, and there are sections that actively contradict each other. If this class wasn’t core (and therefore mandatory), I would have dropped it.
Emerging Technology and Innovation
I really enjoyed this class. The idea here is you complete it in your last semester of uni, and research to a good level of detail some form of emerging technology, or even find a problem and research a novel solution. The research I performed for this was around a passion of mine: helping small businesses prepare their environments for incident response. If you’re interested, this research formed the core of my GCIH Gold paper, and there’ll be a link to that in a future post. This research was wrapped in project management and incremental updates, culminating in a written report and presentation of your findings. It really feels like a course written to give students a taste of the PhD life.
Cyber Warfare and Terrorism
This course was decidedly ok. It leaned a bit too heavily into discussing cyber crime. Once we’d gotten through that, the bulk of our learning was achieved by researching technology used in warfare, and existing cyber-terrorism attacks. Reading books like Countdown To Zero Day: Stuxnet and the Launch of the World’s First Digital Weapon and blogs like Mandiant’s Shamoon blog entry would provide you with a similar level of knowledge.
The prescribed text for this course was Understanding Cyber-Warfare Politics, Policy, and Strategy, and it was ok.
Forensic Investigation
This class felt next to useless. The prescribed text was Guide to Computer Forensics and Investigations, and it’s pretty amazing. There is a caveat on this book that it has some textual errors that give a strong impression that the upgrade from 6e to 7e wasn’t as well edited as it should have been. Despite that, I loved this book. Unfortunately, so did the professor. All the assessment material was taken from this book’s exercises, which felt like cheating, given the cost of this class.
I was also disappointed by the professor. There were a number of instances in the class where when asked questions, the professor clearly didn’t know the answer and tried to either bluff his way through or stuck to the book. Unfortunately, in one instance, the book was also incorrect (some MFT time headers had shifted, which was in keeping with the MFT header format), and the professor backed the book to the hilt despite overwhelming contrary evidence.
